HashiCorp Vault是一款企业级私密信息管理工具。说起Vault,不得不提它的创造者HashiCorp公司。HashiCorp是一家专注于DevOps工具链的公司,其旗下明星级产品包括Vagrant、Packer、Terraform、Consul、Nomad等,再加上Vault,这些工具贯穿了持续交付的整个流程。
为什么使用HashiCorp Vault?
企业内各类私密信息安全存储问题需求,例如:ssh key,各类API认证信息,数据库权限等等
HashiCorp Vault优势
HashiCorp Vault作为集中化的私密信息管理工具,具有以下特点:
- 存储私密信息
不仅可以存放现有的私密信息,还可以动态生成用于管理第三方资源的私密信息。所有存放的数据都是加密的,任何动态生成的私密信息都有租期,并且到期会自动回收。 - 滚动更新秘钥
用户可以随时更新存放的私密信息。Vault提供了加密即服务(encryption-as-a-service)的功能,可以随时将密钥滚动到新的密钥版本,同时保留对使用过去密钥版本加密的值进行解密的能力。 对于动态生成的秘密,可配置的最大租赁寿命确保密钥滚动易于实施。 - 审计日志
保管库存储所有经过身份验证的客户端交互的详细审核日志:身份验证,令牌创建,私密信息访问,私密信息撤销等。 可以将审核日志发送到多个后端以确保冗余副本。
另外,HaishiCorp Vault提供了多种方式来管理私密信息。用户可以通过命令行、HTTP API等集成到应用中来获取私密信息。HashiCorp Vault也能与Ansible、Chef、Consul等DevOps工具链无缝结合使用。
HashiCorp Vault实践
1 | [root@node01 ~]# wget https://releases.hashicorp.com/vault/1.4.0/vault_1.4.0_linux_arm64.zip |
运行起来后检查下应用信息
1 | [root@node01 ~]# vault status |
UI界面体验
登陆地址: http://{ip}:8200/ui/
启动后默认会生成一个token信息,每次都会变化,使用该token登陆。Vault支持很多主流认证方式,根据需要增加其他认证方式,本人测试使用的是OpenLDAP。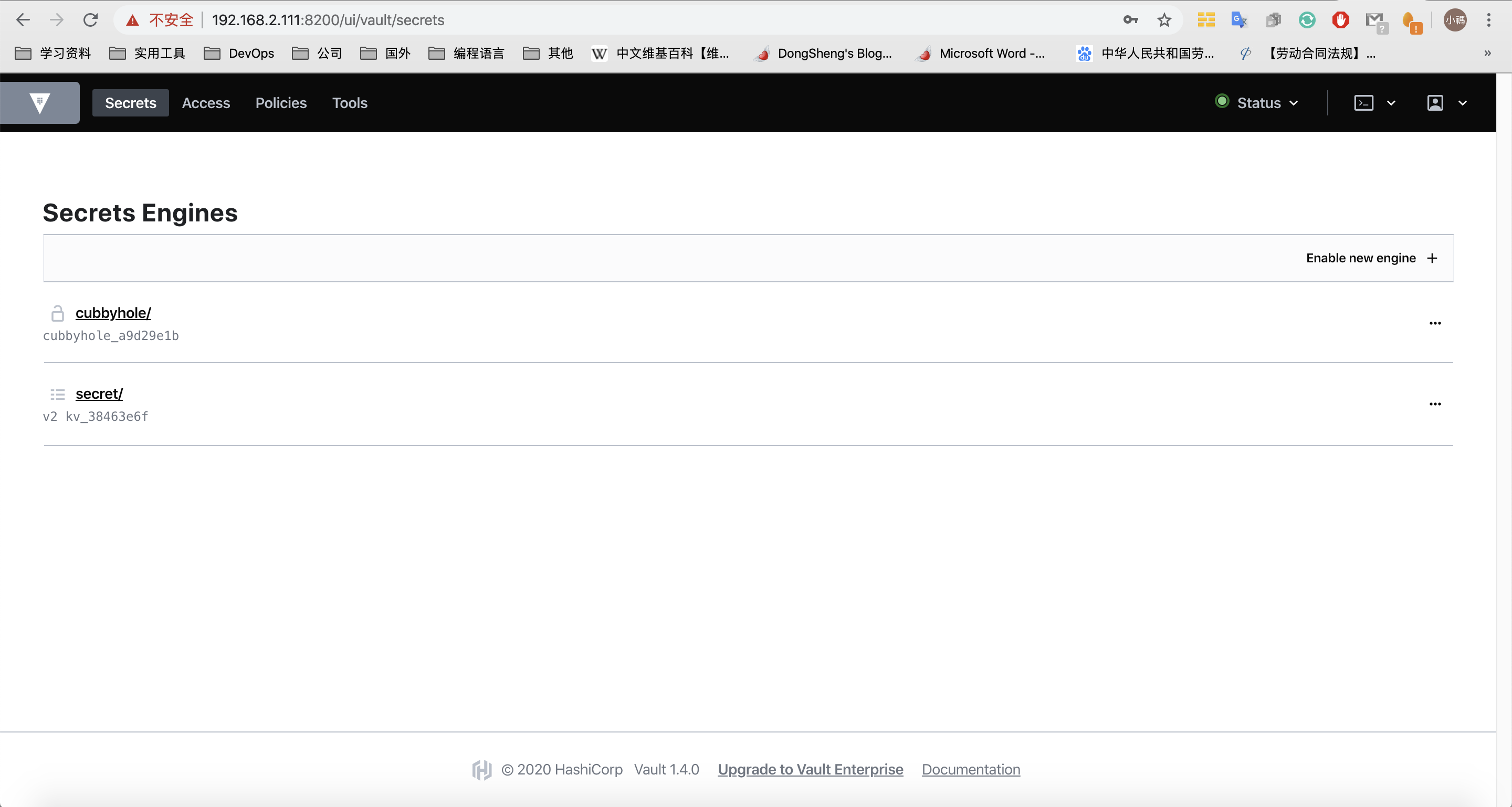
支持的密钥引擎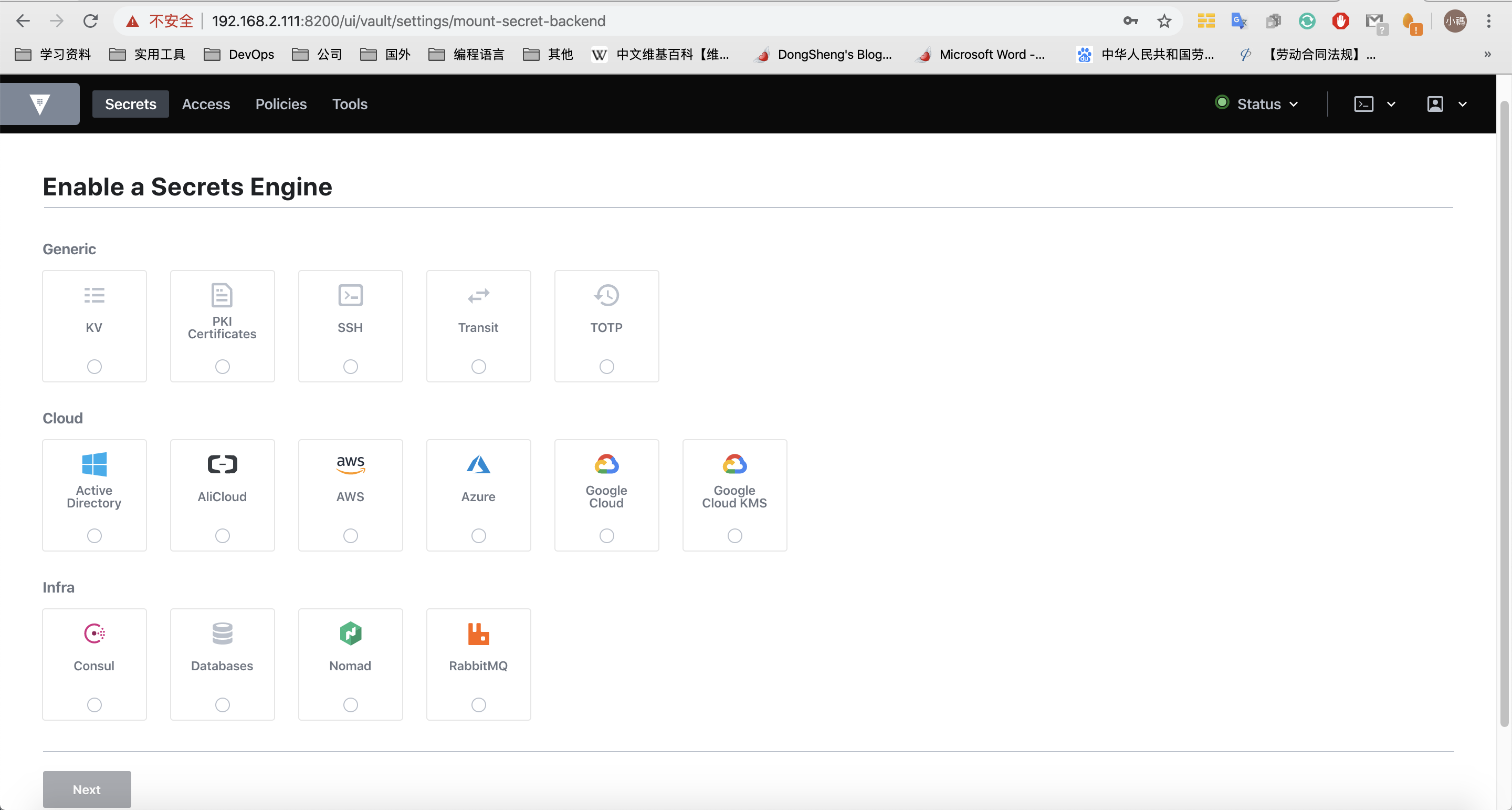
界面就这么内容,很多操作还是依赖于命令行操作。
启用OpenLDAP认证
1 | vault auth enable ldap |
修改配置信息重新执行命令即可更新
业务实践
基于Vault实现Linux服务器一次性SSH密码登陆
参考资料
======================================================
希望各位朋友支持一下
- 领取我的阿里云幸运券,谢谢.
- 使用腾讯云资源
- Linode VPS
- 搬瓦工VPS
- 阿里云1888元云产品通用代金券点我
- 阿里云最新活动全民云计算升级-拼团上云更优惠
- 今日头条
本文作者:dongsheng
本文地址: https://mds1455975151.github.io/archives/ff02dc0f.html
版权声明:转载请注明出处!


